Our vision
We aim to deliver advanced cybersecurity solutions that protect critical assets, ensure compliance, and prevent evolving threats. By combining cutting-edge technology with proactive strategies, we strive to be the trusted partner that safeguards organizations, enabling them to focus on growth and innovation without compromising security.
AI vision


We help organizations stay secure, resilient, and compliant
At Trinet Technologies, we take a comprehensive approach to cybersecurity—one that blends prevention, detection, and response with strategic foresight. Our goal is not only to neutralize threats, but to strengthen enterprise-wide resilience and ensure uninterrupted business continuity.
We work closely with security leaders to assess vulnerabilities, reduce attack surfaces, and embed robust governance frameworks. By aligning security with business priorities, we help enterprises adapt to emerging risks while maintaining trust, compliance, and competitive strength.
- Our mission
We secure your systems, data, and users from evolving threats—ensuring business continuity and minimal disruption.
With real-time detection and automated response, we stop threats before they become incidents.
We align your security posture with global standards, building trust and ensuring regulatory compliance.
- Our capabilities
Our core services
Threat detection
We provide intelligent, real-time threat detection and automated response capabilities to safeguard your digital ecosystem. Using advanced security analytics, behavioral monitoring, and threat intelligence, we identify anomalies early and take immediate action to contain and eliminate threats.
Security architecture
Our cybersecurity architects develop future-ready security frameworks grounded in zero-trust principles, identity access management, and layered defense models. We assess your current infrastructure, define clear security roadmaps, and implement scalable solutions that evolve with your business.
Risk management
Trinet Technologies helps you stay ahead of evolving regulatory demands while minimizing organizational risk. We conduct in-depth audits, map your controls to global standards like ISO 27001, NIST, GDPR, and HIPAA, and close compliance gaps with structured policy development.
Secure your future
Build a resilient digital foundation that defends against evolving cyber threats while enabling innovation and growth.
- Protect critical systems and data with next-gen security architecture that strengthens your digital core.
- Ensure business continuity with proactive threat detection, response, and recovery strategies across your entire enterprise.
- Drive customer trust and regulatory compliance through airtight security governance and zero-trust principles.
- Empower your teams with secure-by-design tools and training to create a culture of cyber awareness and accountability.

Rising threat landscape
Global Cybersecurity Market Projected to Reach $538.3 Billion by 2030.
With growing digital adoption comes rising cyber complexity and risk:
- Evolving Threat Vectors: From ransomware to supply chain attacks, threat actors are becoming more sophisticated, targeting vulnerabilities across hybrid environments.
- Compliance Burdens: Regulations like GDPR, HIPAA, and ISO 27001 demand constant monitoring and timely reporting—placing pressure on IT and legal teams.
- Visibility Challenges: Disconnected systems and shadow IT reduce visibility, increasing the risk of misconfigurations, insider threats, and unauthorized access.
- Incident Response Gaps: Without automated threat intelligence and integrated response playbooks, even minor breaches can escalate into critical failures.
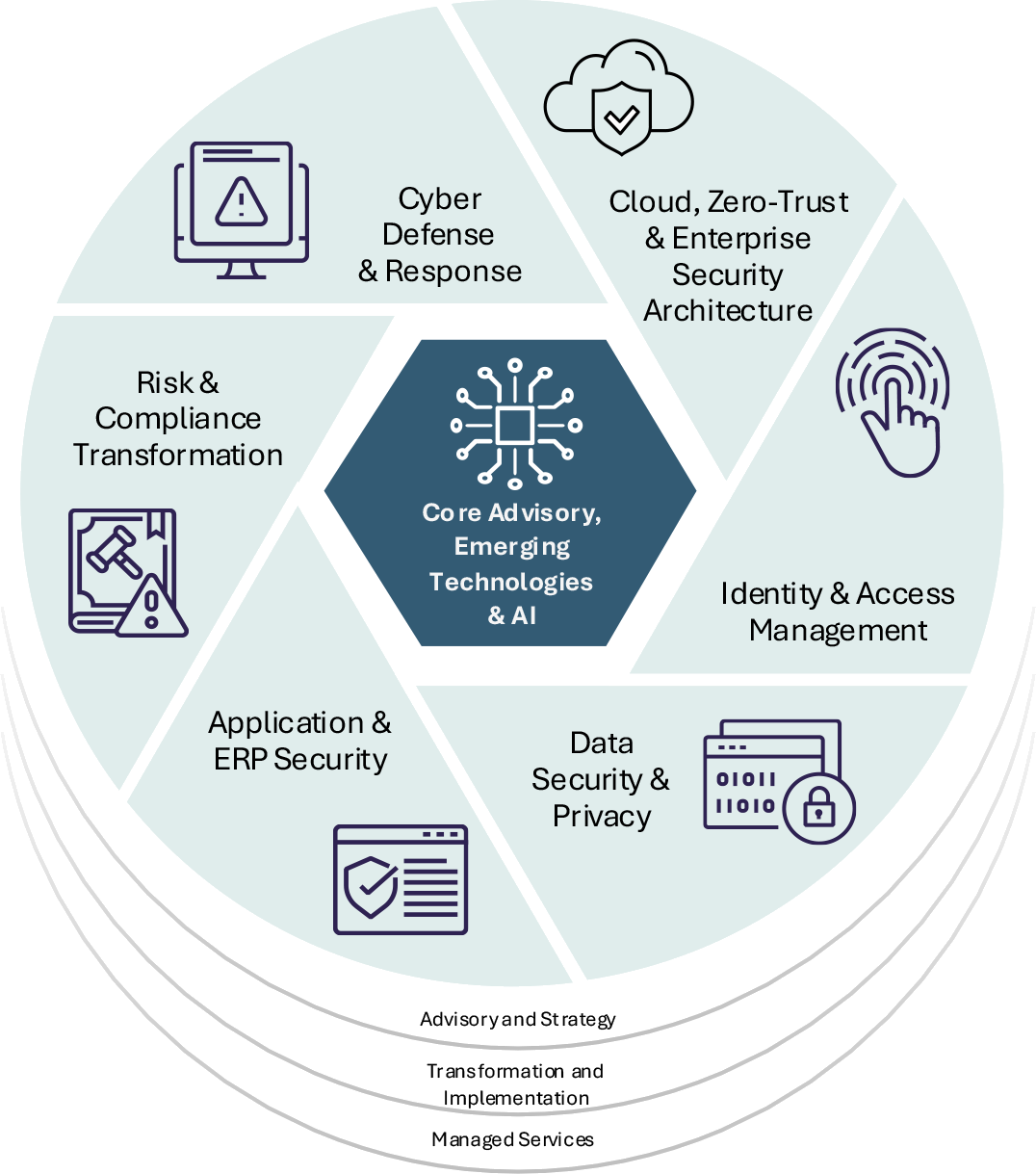
Future-ready protection
Redefine what security means for a digital-first world.
- Expand securely across geographies and ecosystems
- Build adaptable security models to support growth
- Harness AI and analytics for smarter threat prediction
- Drive innovation without compromising on protection
- Transform security from a cost center into a value enabler

Navigate cyber risk with confidence
Our experts help you identify risk exposure, benchmark security maturity, and implement tailored roadmaps with actionable insights. From posture assessments to resilience planning, we deliver the frameworks and tools to secure your enterprise—today and for the future.

Our process
Assessing your security landscape
We begin by understanding your existing infrastructure, digital assets, regulatory environment, and risk exposure. This helps us identify vulnerabilities, gaps, and business-critical priorities that shape your cybersecurity roadmap.
Designing the defense strategy
Our experts architect a tailored security strategy aligned with your operations and compliance needs. We design layered defense models, zero-trust frameworks, and response protocols that scale with your organization.
Implementing protection mechanisms
From endpoint security to identity management and SIEM integration, we implement tools, technologies, and policies that fortify your systems. Our rollout is planned to minimize disruption while maximizing protection.
Monitoring, managing & evolving
We provide 24/7 monitoring, threat detection, and response services. Our continuous improvement model ensures your security environment adapts to emerging threats and keeps pace with evolving regulations.
- What we believe
Do what is right, always
At Trinet Technologies, doing the right thing is not just a principle—it is the foundation of everything we do. Whether we are making business decisions, working with clients, or building new technologies, we choose honesty, fairness, and responsibility. We believe success means little without integrity, and that doing what is right is always the best path forward—even when no one is watching.
This belief shapes our culture, our partnerships, and our daily actions. It guides how we treat people, how we approach challenges, and how we measure impact. In a fast-changing world, we stay grounded in our values, committed to building trust and doing meaningful work—for our team, our clients, and the communities we serve.
Case studies
How we help
Trinet Technologies delivers enterprise-grade cybersecurity services that enable organizations to grow with confidence, innovate securely, and stay resilient in a constantly evolving threat landscape. From securing cloud workloads to building proactive defense strategies, we make cybersecurity a foundation for business success—not a limitation.



150+
100+
We provide strategic, transformational, and technical cybersecurity solutions
- Our approach
Our approach to enterprise-grade cybersecurity
Threat prevention & response
Our cybersecurity framework is built on proactive defense. We implement advanced threat detection systems, endpoint protection, and automated response capabilities to help businesses prevent, detect, and neutralize attacks before they impact operations.
Security architecture & zero trust
We design robust, scalable security architectures that are tailored to your enterprise needs. Using a zero-trust model, we help you protect critical assets, secure user access, and create a layered defense that adapts to modern hybrid and cloud environments.
Governance, risk & compliance
Our experts help organizations achieve compliance with global standards like ISO 27001, GDPR, HIPAA, and NIST. We assess gaps, define risk frameworks, and implement controls that not only meet regulatory expectations but strengthen operational integrity.
Incident management & resilience
We provide incident response planning, breach simulations, and forensic analysis to help organizations prepare for and recover from security events. Our approach focuses on minimizing downtime, maintaining reputation, and restoring business continuity at speed.
- Client success in risk management and compliance
Reduction in incident response time
We partnered with Bharti Airtel to implement a real-time Security Operations Center (SOC) backed by AI-driven threat detection and automated response mechanisms. The initiative led to a 70% drop in average incident response time, while significantly enhancing visibility and control across their multi-region telecom infrastructure.
Infrastructure uptime achieved
IndusInd Bank collaborated with us to strengthen its cybersecurity landscape through a multi-layered defense strategy spanning cloud and on-premise systems. Our solution enabled ISO 27001 compliance, ensured 99.99% uptime, and supported seamless navigation of regulatory audits.
Countries secured with unified governance
We helped Ashok Leyland implement a global cybersecurity framework across operations in more than 30 countries. This involved deploying unified access controls, enterprise-grade endpoint protection, encryption protocols, and a centralized compliance governance model—standardizing security while empowering local agility.
How we work
Delivering enterprise-grade cybersecurity with precision, foresight, and accountability. Partner with us to secure your digital future.
Designed for resilience
Driven by impact
Certified experts
No endpoints
- Our four key pillars

We build cybersecurity frameworks that are resilient by design—engineered to detect, contain, and respond to threats in real time. Every solution is tailored to withstand the most advanced and persistent attacks.
- Zero-trust architecture with identity-first security
- Real-time threat detection and response layers
- Adaptive controls for hybrid and cloud environments

Our approach ensures your security posture is built to scale—without compromising on performance. We help enterprises embed protection deep within networks, workloads, and endpoints.
- Distributed and fault-tolerant security systems
- Cloud-native protection for dynamic infrastructure
- Scalable solutions for multi-location enterprises

We believe the strongest security begins with awareness. We equip teams with the right tools, training, and policies to act as the first line of defense.
- Role-based access and authentication frameworks
- Company-wide cybersecurity awareness programs
- Insider threat prevention and employee risk scoring

We help enterprises meet global security standards and maintain continuous audit readiness through strategic governance and automated compliance frameworks.
- Alignment with ISO 27001, NIST, GDPR, HIPAA, and SOC 2
- Automated policy enforcement and audit logs
- Comprehensive risk, privacy, and control frameworks
- Our industries
Client results
Discover how we help clients achieve business growth through tailored technology solutions.
Related insights
We are here to address any questions you may have as you implement your plan. Additionally, for clients seeking an ongoing partnership, explore our comprehensive Services.










